Actually, I think from what I'm seeing that it may not exactly be a synflood targeting Libero. I think Libero may be being (ab)used to do massive portscanning or similar.
Image should be visible below - it's normal statistics for the 18th through say, part of the 21st, messed up 22ed - 24th and on the 24th me trying different things in an attempt to mitigate (graph is from yesterday). Look at the SYN_SENT2 maximum.
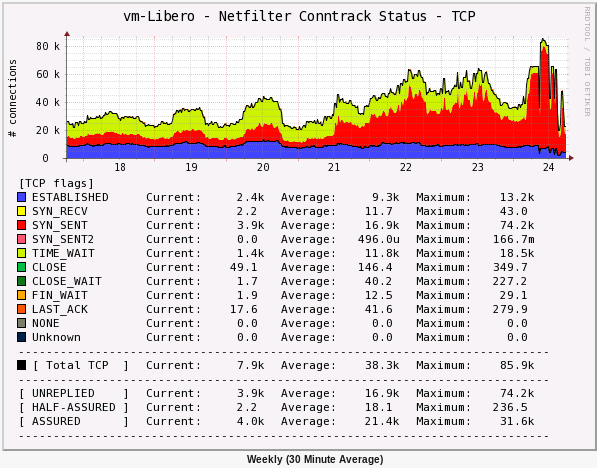
When it's happening it can look like this:
# netstat -n | grep -c SYN
17696
#
Also one tiny part of the netstat looked like this:
tcp 0 1 64.113.32.29:33354 <external IP munged>:81 SYN_SENT
tcp 0 1 64.113.32.29:39659 <external IP munged>:8888 SYN_SENT
tcp 0 1 64.113.32.29:44247 <external IP munged>:87 SYN_SENT
tcp 0 1 64.113.32.29:42038 <external IP munged>:8888 SYN_SENT
tcp 0 1 64.113.32.29:42077 <external IP munged>:83 SYN_SENT
tcp 0 1 64.113.32.29:36282 <external IP munged>:8888 SYN_SENT
tcp 0 1 64.113.32.29:46023 <external IP munged>:8888 SYN_SENT
Port 8888 is supposedly opened up for listen by a virus.